Banner

Online Article

-
What Are TTPs and How Understanding Them Can Help Prevent the Next IncidentTTP analysis can help security teams detect and mitigate attacks by understanding the way threat actors operate. Below we define the three elements of TTPs: tactics, techniques, and procedures.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 6

-
THREAT HUNTING:10 ADVERSARY BEHAVIORS TO HUNTYou’re ready to make the jump from alert-based Investigations to threat hunting. But what should you hunt for? How do you perform the hunts? What data will you need to collect?
This is often the greatest question you will need to answer as a hunter. To get you on the right track, I have curated several techniques that might pique your interest.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 7

-
Different Types of Hackers ExplainedThere are many types of hackers, like white hats, black hats, grey hats, script kiddies, and hacktivists. Contrary to popular opinion, not all hackers are bad, and each type has a specific role and target.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 13
-
Reconnaissance & ToolsThe first stage of ethical hacking is information gathering so the other name of information gathering is known as Reconnaissance
Reconnaissance: Information Gathering and getting to know the target systems is the first process in ethical hacking. Reconnaissance is a set of processes and techniques (Footprinting, Scanning & Enumeration) used to covertly discover and collect information about a target system.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 17 & 30
-
Scope and Limitations of Ethical HackingScope and Limitations of Ethical Hacking, It is a structured and organized security assessment, usually as part of a penetration test. Security audit and is a crucial component of risk assessment, and information systems security best practices.
It is used to identify risks and highlight remedial actions, and also to reduce Information and Communications Technology (ICT) costs by resolving those vulnerabilities.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 26
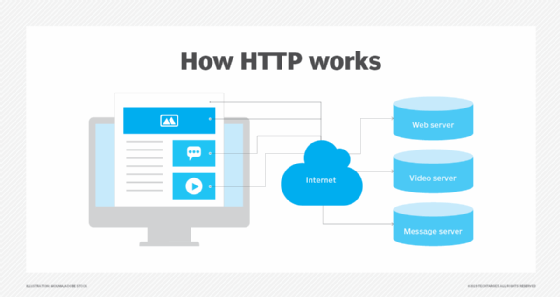
-
Google dork queryGoogle dorking, also known as Google hacking, can return information difficult to locate through simple search queries. This includes information not intended for public viewing, but that is inadequately protected and can, therefore, be "dorked" by a hacker.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 29
eBooks
-
Gray Hat Hacking: the Ethical Hacker's Handbook, Fifth Edition by Up-to-date strategies for thwarting the latest, most insidious network attacks This fully updated, industry-standard security resource shows how to fortify computer networks by learning and effectively applying ethical hacking techniques. Based on critical topics that the authors teach at major security conferences and colleges, the book features actionable planning and analysis methods as well as practical steps for identifying and combating both targeted and opportunistic attacks. Gray Hat Hacking: The Ethical Hacker's Handbook, Fifth Edition, clearly explains the enemy's devious weapons, skills, and tactics and offers field-tested remedies, case studies, and interesting labs. You will get complete coverage of penetration testing, vulnerability discovery, malware analysis, reverse engineering, and Internet of Things security. State-of-the-art mobile exploits, ransomware, and legal issues are thoroughly explained. * Fully revised content--features 13 brand-new chapters * Includes current techniques to analyze and block ransomware * Written by a team of computer security experts
ISBN: 9781260108415Publication Date: 2018-06-08
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 13
-
Ethical hacking a hands-on introduction to breaking in by A hands-on guide to hacking computer systems from the ground up, from capturing traffic to crafting sneaky, successful trojans. A crash course in modern hacking techniques, Ethical Hacking is already being used to prepare the next generation of offensive security experts
ISBN: 9781718501881Publication Date: 2021-11-02
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 23
Videos

-
The Cyber Kill ChainToday my topic is the Cyber Kill Chain, a seven-stage cyberattack process, and a defense model used for the identification and prevention of cyber-attacks on a computer network.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 5

-
Ethical Hacking In 2 Minutes | What Is Ethical Hacking? | Ethical Hacking Explained | SimplilearnIn this Simplilearn video on Ethical Hacking in 2 Minutes, you will get a quick glimpse of the ethical hacking process.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 23

-
Enumeration Definition, Types, and TechniquesWe'll dive into the topic of the types and techniques of enumeration in cyber security.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 34
Infographic
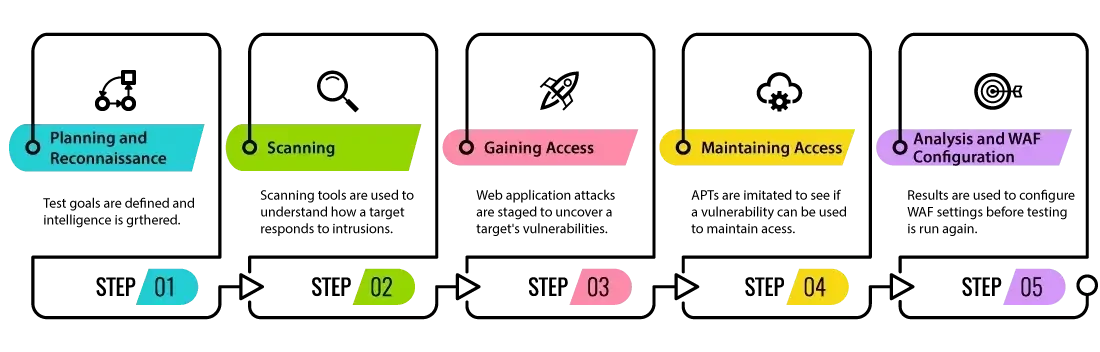
-
What is Ethical Hacking?The ethical hacking process begins with looking for various ways to hack into the system, exploiting vulnerabilities, maintaining steady access to the system.
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 16
Note: Refer to MHE Lecture 2- Introduction to Ethical Hacking Essential: Slide 24

