Online Articles
Refer to FCN Lecture 5- Security Network Domain: Slide 3
Refer to FCN Lecture 5- Security Network Domain: Slide 6
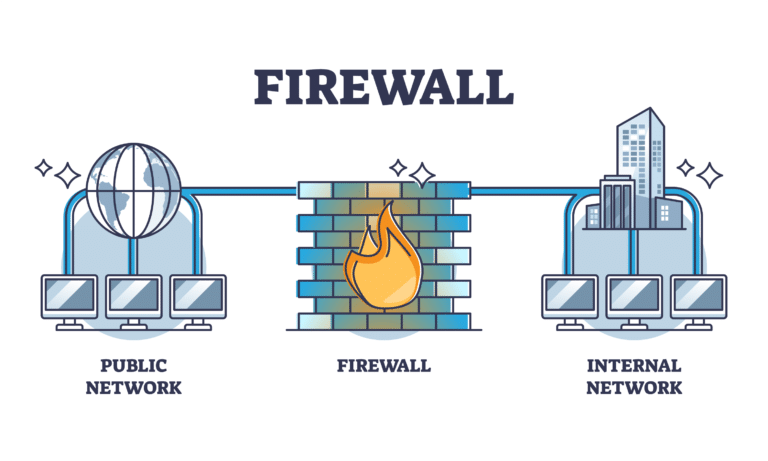
Firewalls are designed to act as a barrier between your network and the internet. They analyse incoming and outgoing traffic and evaluate it against set criteria to decide whether it is potentially harmful. Firewalls block data, which is considered to be a threat, from entering your network, whilst data that is deemed safe is sent on to its intended destination.
When you have an internet connection it is effectively an open path into your network, giving someone plenty of opportunity to attack and access your personal data. Installing a firewall makes this virtually impossible as it closes the path and provides a layer of security before allowing someone to access your network.
Refer to FCN Lecture 5- Security Network Domain: Slide 15
Refer to FCN Lecture 5- Security Network Domain: Slide 20
Refer to FCN Lecture 5- Security Network Domain: Slide 22
Videos
41. CAMBRIDGE IGCSE (0478-0984) 3.4 Network interface card (NIC) by Craig'n'Dave
This video introduces Network Interface Card (NIC).
Refer to FCN Lecture 5- Security Network Domain: Slide 7
MAC Address Explained by PowerCert
What is a MAC address? What is the difference between an IP address and a MAC address? The MAC or media access control address is an identifier that every network device uses to uniquely identify itself on a network.
Refer to FCN Lecture 5- Security Network Domain: Slide 9
Denial of Service Attacks Explained by IBM Technology
Denial of Service attacks are one of the many tactics malicious actors may use. In this video Jeff Crume explains the different types of DoS attacks and what kind measures can be taken to mitigate the threat posed by these kinds of attacks.
Refer to FCN Lecture 5- Security Network Domain: Slide 23
DDoS Attack Explained by PowerCert Animated Video
What is a DDoS attack? This is an animated video explaining what a DDoS attack is. Distributed denial of service. It also explains what is a botnet.
Refer to FCN Lecture 5- Security Network Domain: Slide 24
Infographic
 lgatelecom. Understanding Cyber Security:Man-in-the-Middle (MitM) Attack [Infographic].
lgatelecom. Understanding Cyber Security:Man-in-the-Middle (MitM) Attack [Infographic].
Refer to FCN Lecture 5- Security Network Domain: Slide 25 and 26