Banner

Online Articles
- How to Tell If Your Computer Has a Virus and What to Do About ItCOMPUTER VIRUSES MAKE YOUR DEVICES SICK, BUT YOU CAN USUALLY HELP THEM HEAL IF YOU ACT FAST.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 21
- Commentary: ‘We won’t pay’ - ransom negotiations in cyberattacks aren’t so straightforwardA ransomware task force in Singapore has recommended that it be made mandatory for companies to report ransom payments. Sygnia’s vice president of cyber security service in APAC weighs up the considerations behind ransom payments.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 27

- What is Rootkit – Definition and ExplanationA rootkit is a type of malware designed to give hackers access to and control over a target device. Although most rootkits affect the software and the operating system, some can also infect your computer’s hardware and firmware.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 32
- MOST COMMON TYPES OF CYBER VULNERABILITIESA vulnerability in cybersecurity is a weakness in a host or system, such as a missed software update or system misconfiguration, that can be exploited by cybercriminals to compromise an IT resource and advance the attack path.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 54

- Information disclosure vulnerabilitiesIn this section, we'll explain the basics of information disclosure vulnerabilities and describe how you can find and exploit them. We'll also offer some guidance on how you can prevent information disclosure vulnerabilities in your own websites.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 58
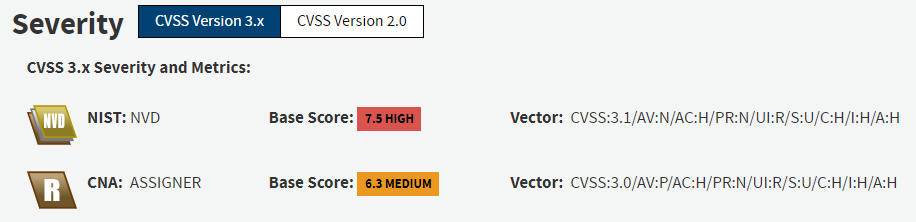
- Understanding Vulnerability Detail PagesThese serve as a summary of the vulnerability and can include information such as the vulnerable product, impacts, attack vector, weakness or other relevant technical information.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 65
- 17 Best Vulnerability Assessment Scanning ToolsVulnerability scanning or vulnerability assessment is a systematic process of finding security loopholes in any system addressing the potential vulnerabilities.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 75
LinkedIn Learning

- The key elements of VM: DARC - Learning Vulnerability Management Video Tutorial | LinkedIn Learning, formerly Lynda.comThis course provides those without prior experience in the area an overview of why vulnerabilities exist, as well as an explanation of the process of managing them from start to finish.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 72
eBook
Ransomware revealed a beginner's guide to protecting and recovering from ransomware attacks by
ISBN: 9781484242551Publication Date: 2019-11-07
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 27
Videos

- Internet Worm Maker | How To Make Worm VirusA computer worm is a self-replicating malware that duplicates itself to spread to uninfected computers. An Internet worm is a type of malicious software (malware) that self-replicates and distributes copies of itself to its network.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 31
- What Is Botnet? | What Is Botnet And How It Works? | Botnet Explained | Botnet Tutorial |SimplilearnThis video on 'What is a botnet?' will we understand what a botnet is and how they work by infecting vulnerable devices and getting them under the control of the botnet server.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 40

- Performing Vulnerability AssessmentsWe'll dive into the topic of performing vulnerability assessments.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 62

- What is CVE? | Common Vulnerabilities and ExposuresVulnerability Management is one of the key services which SOC has to offer. We are starting off with very basics, I mean knowing what a vulnerability is, and then slowly we transition to designing and building Security Operations Center.
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 66

- GFI LanGuard Review: Top Features, Pros, And ConsThis video reviews GFI LanGuard, a popular vulnerability and patch management tool. Looking for a security solution?
Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 74
Infographics

Note: Refer to MHE Lecture 3- Information Security Threats and Vulnerability Assessment: Slide 12




