Banner

Online articles
Refer to FCN Lecture 6- Security in Software Domain: Slide 6
|
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. |
Refer to FCN Lecture 6- Security in Software Domain: Slide 9
|
Session vs. Cookies| Difference between Session and Cookies The Session and cookies are used by different websites for storing user's data across different pages of the site. Both session and cookies are important as they keep track of the information provided by a visitor for different purposes. The main difference between both of them is that sessions are saved on the server-side, whereas cookies are saved on the user's browser or client-side. |
Refer to FCN Lecture 6- Security in Software Domain: Slide 22
Refer to FCN Lecture 6- Security in Software Domain: Slide 26
Videos
XSS - Cross Site Scripting Explained by Virtual Forge an Onapsis Company
This VirtualForge cartoon video provides an overview of how XSS works and how malicious hackers can exploit an XSS vulnerability to gain access to enterprise applications and sensitive data.
Refer to FCN Lecture 6- Security in Software Domain: Slide 15
Cross Site Request Forgery (CSRF or XSRF) by CyberShaolin
Reuben Paul (@RAPst4r) describes what a Cross Site Request Forgery (CSRF) attack is and how it works.
Refer to FCN Lecture 6- Security in Software Domain: Slide 24
How to Prevent CSRF - Explained In Less Than 5 Minutes by Crashtest Security
We've already explained what a Cross-Site Request Forgery is in one of our other videos. Now we dive into the topic of how to best prevent a CSRF Attack.
Refer to FCN Lecture 6- Security in Software Domain: Slide 25
Infographic
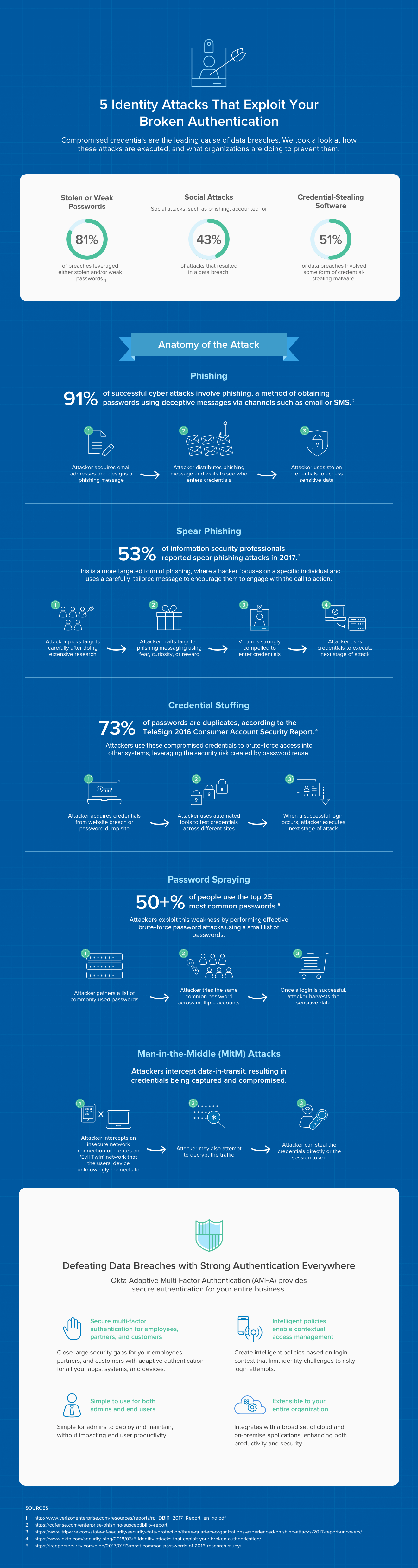 Okta. 5 Identity Attacks That Exploit Your Broken Authentication [Infographic].
Okta. 5 Identity Attacks That Exploit Your Broken Authentication [Infographic].
Refer to FCN Lecture 6- Security in Software Domain: Slide 18