

Online Articles
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 9
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 17
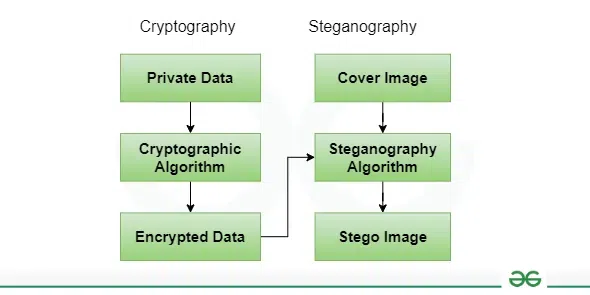
What is the difference between Encryption and Steganography in Information Security?
Encryption
Data encryption is a method of translating information from plaintext (unencrypted) to ciphertext (encrypted). Users can access encrypted information with an encryption key and decrypted information with a decryption key. There are large amounts of sensitive information handled and stored online in the cloud or on combined servers. Encryption needs cybersecurity to protect against brute-force and cyber-attacks, such as malware and ransomware. Data encryption operates by protecting transmitted digital information on the cloud and computer systems. There are two types of digital information, transmitted information or in-flight information and stored digital information or data at rest.
Steganography
Steganography is a technique that facilitates concealing of a message that is to be kept secret within other message. This result is the concealment of the hidden message itself. Steganography techniques can be used to images, a video file or an audio file. The main objective of steganography is to connect securely in a completely undetectable manner and to prevent drawing suspicion to the transmission of a hidden information. It is not to maintain others from understanding the hidden information, but it is to keep others from thinking that the data even exists. If a steganography method generates someone to suspect the carrier medium, thus the method has declined.
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 27
Infographics

TechTarget. What is plaintext? [Infographic].
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 9
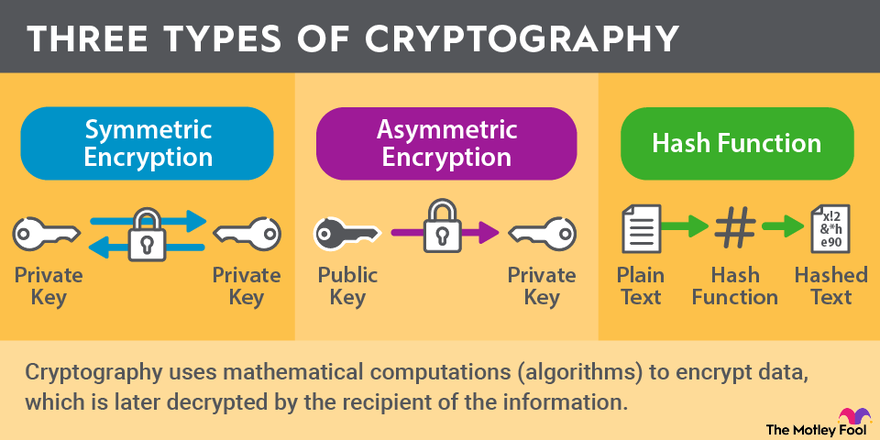
The Motley Fool (2022, 27 June). What Is Cryptography? [Infographic].
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 12
Videos
SCYTALE CIPHER EXPLAINED!!! by Cryptography Home
A brief but indepth discussion of the historical 400BC Scytale cipher discussing how it works and techniques to help one understand it better.
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 4
Rivest Cipher 4 Explained by Crashtest Security
We'll dive into Rivest Cipher 4 and how the RC4 encryption works.
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 16
Difference between Substitution Cipher and Transposition Cipher | Substitution vs Transposition by Chirag Bhalodia
Difference between Substitution Cipher and Transposition Cipher.
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 18 & 19
Steganography - SY0-601 CompTIA Security+: 2.8 by Professor Messer
In this video, you’ll learn about obfuscation, steganography, and how to hide data inside of image, audio, and video files.
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 26
eBooks
Introduction to Cryptography by This book introduces readers to perhaps the most effective tool in achieving a secure environment, i.e. cryptography.
ISBN: 9781351628136Publication Date: 2018-07-10
Note: Refer to FCN Lecture 4- Security in Data Domain: Slide 9