
Online Articles
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 16
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 23
eBooks
Cyberjutsu : Cybersecurity for the Modern Ninja by Cyberjutsu is a practical cybersecurity field guide based on the techniques, tactics, and procedures of the ancient ninja. Cyber warfare specialist Ben McCarty's analysis of declassified Japanese scrolls will show how you can apply ninja methods to combat today's security challenges like information warfare, deceptive infiltration, espionage, and zero-day attacks.
ISBN: 9781718500556Publication Date: 2021-04-26Social Engineering by Manipulative communication—from early twentieth-century propaganda to today's online con artistry—examined through the lens of social engineering. The United States is awash in manipulated information about everything from election results to the effectiveness of medical treatments. Corporate social media is an especially good channel for manipulative communication, with Facebook a particularly willing vehicle for it. In Social Engineering, Robert Gehl and Sean Lawson show that online misinformation has its roots in earlier techniques: mass social engineering of the early twentieth century and interpersonal hacker social engineering of the 1970s, converging today into what they call “masspersonal social engineering.” As Gehl and Lawson trace contemporary manipulative communication back to earlier forms of social engineering, possibilities for amelioration become clearer. The authors show how specific manipulative communication practices are a mixture of information gathering, deception, and truth-indifferent statements, all with the instrumental goal of getting people to take actions the social engineer wants them to. Yet the term “fake news,” they claim, reduces everything to a true/false binary that fails to encompass the complexity of manipulative communication or to map onto many of its practices. They pay special attention to concepts and terms used by hacker social engineers, including the hacker concept of “bullshitting,” which the authors describe as a truth-indifferent mix of deception, accuracy, and sociability. They conclude with recommendations for how society can undermine masspersonal social engineering and move toward healthier democratic deliberation.
ISBN: 9780262368926Publication Date: 2022
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 1
Videos
Tailgating and Piggybacking - Social Engineering Tactics Explained by LabCyber
In today's video, I am going to be discussing two very common forms of social engineering which are tailgating piggybacking. These tactics are often used by cyber criminals to gain unauthorized access into secure buildings and rooms.
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 15
How to avoid falling for phishing scams by Channel News Asia
Here's a quick guide on what you can do to avoid falling victim to phishing attempts.
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 17
What is Spear Phishing | Difference from Phishing and Whaling by MalwareFox
In this video, you will know what spear phishing is, and its difference from phishing and whaling.
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 21
Infographics
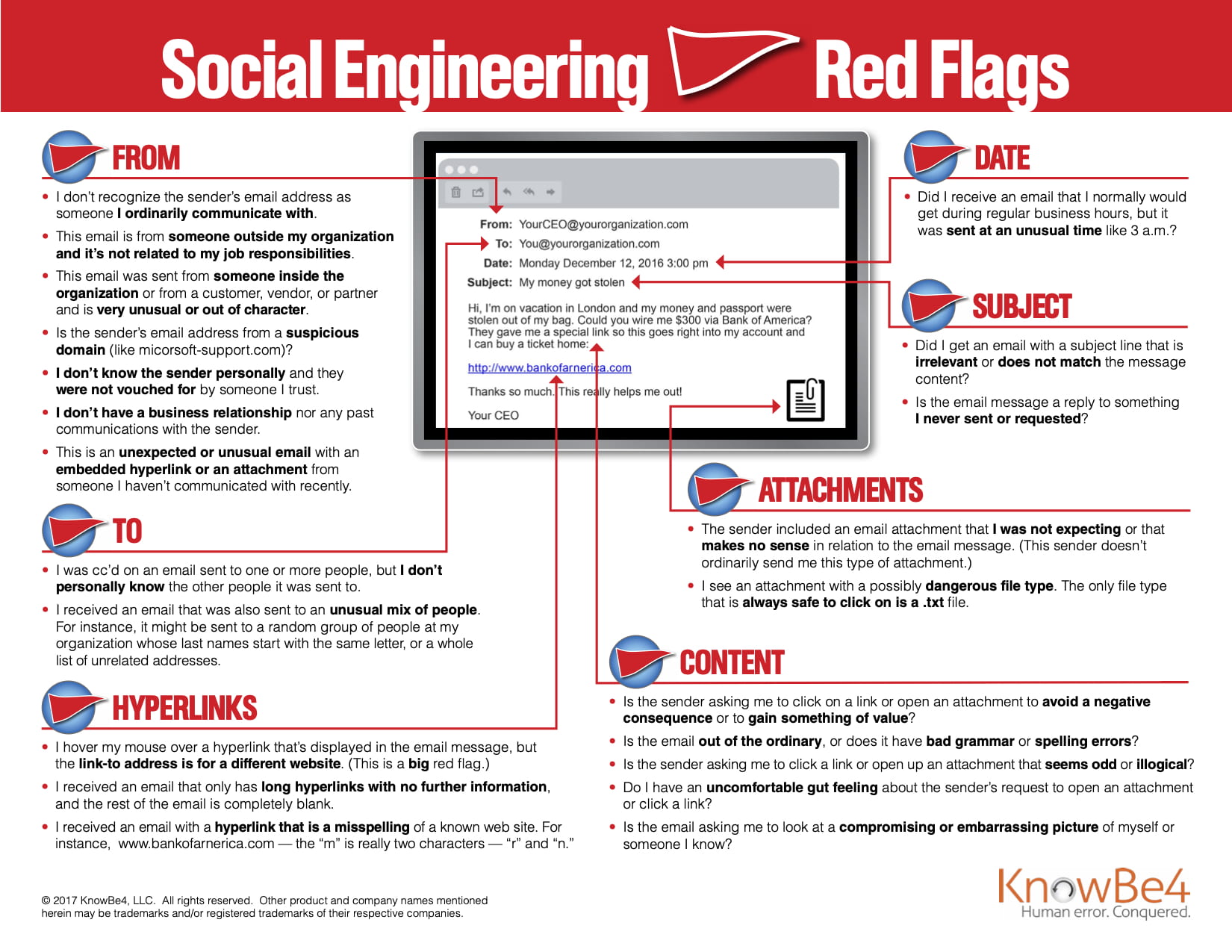 Information Security (2020, May 20). INFOGRAPHIC: 22 Social Engineering Red Flags [Infographic].
Information Security (2020, May 20). INFOGRAPHIC: 22 Social Engineering Red Flags [Infographic].
Note: Refer to FCN Lecture 2- Cybersecurity in User Domain: Slide 19